Product docs and API reference are now on Akamai TechDocs.
Search product docs.
Search for “” in product docs.
Search API reference.
Search for “” in API reference.
Search Results
results matching
results
No Results
Filters
Deploy GlusterFS Cluster through the Linode Marketplace
Quickly deploy a Compute Instance with many various software applications pre-installed and ready to use.
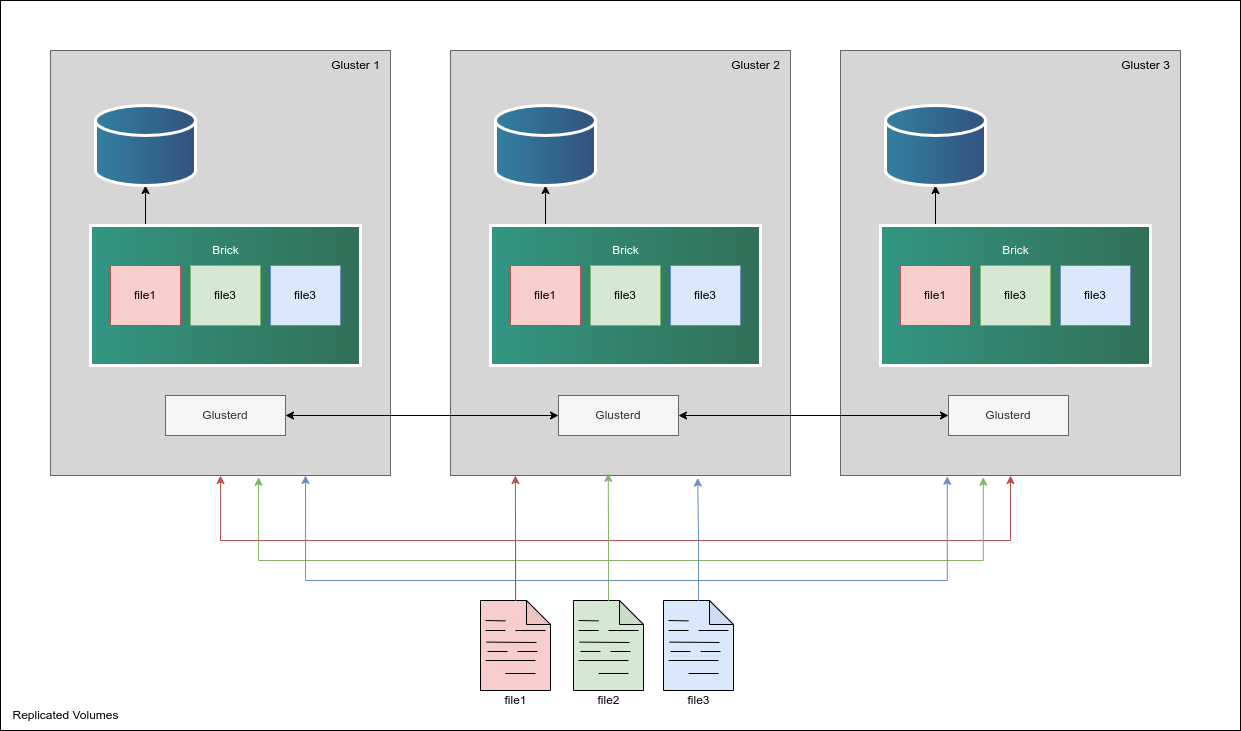
Cluster Deployment Architecture

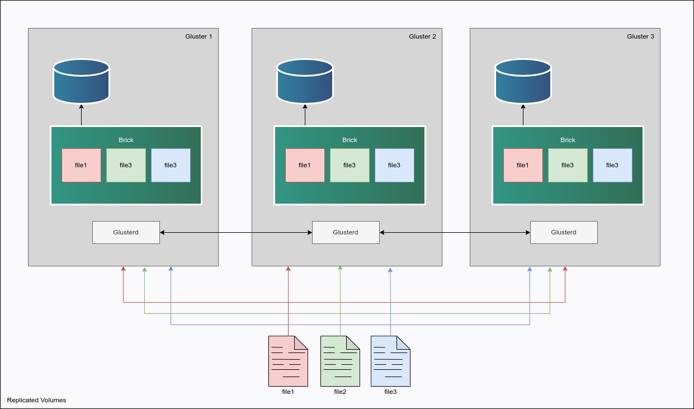
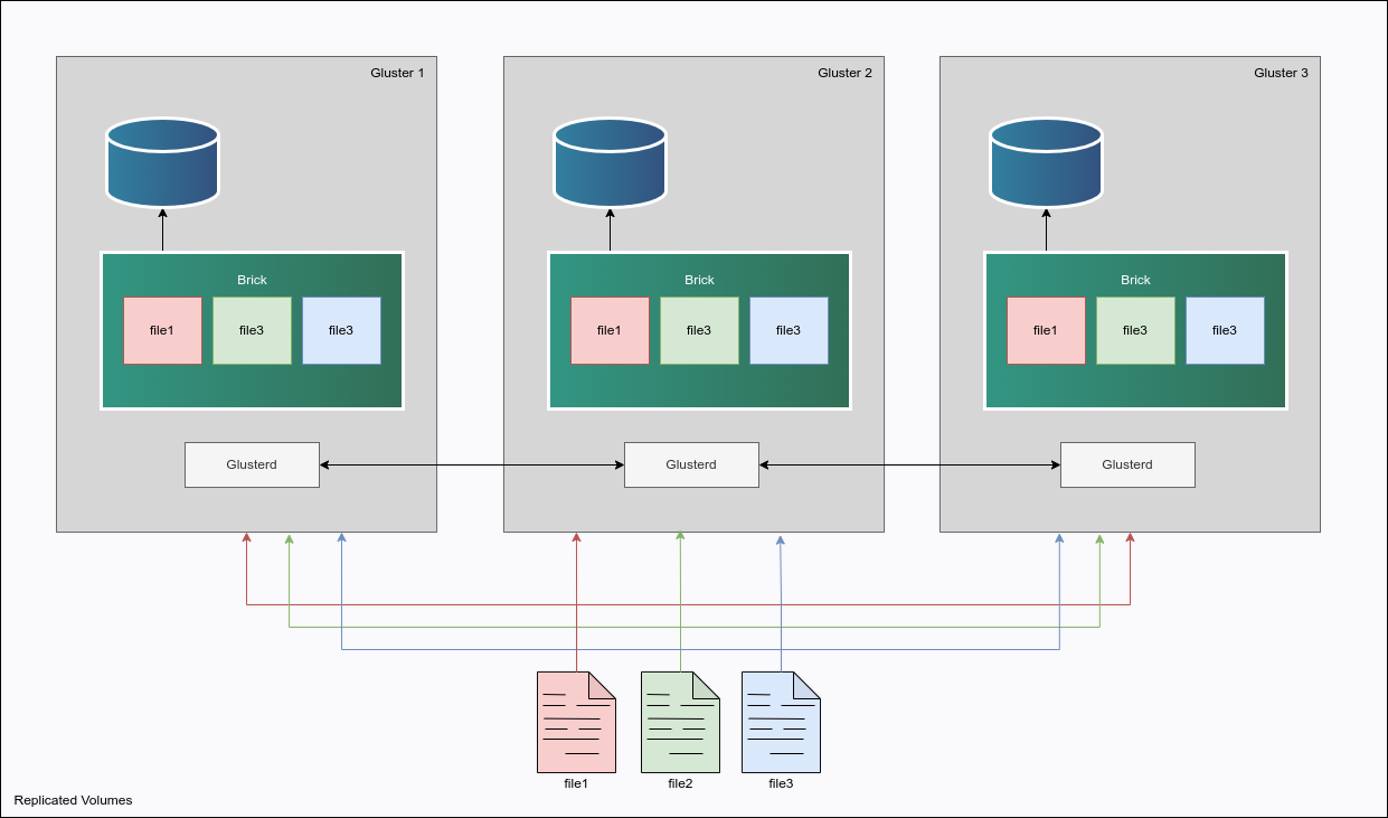
GlusterFS GlusterFS is an open-source, distributed network filesystem designed to scale out and handle large amounts of data across compute instances. It replicates data across multiple GlusterFS servers into a single application mount point, allowing seamless access to files to client instances. With its flexible architecture and ability to replicate data across nodes, GlusterFS provides high availability and fault tolerance, making it suitable for cloud storage and high availability architectures.
Deploying a Marketplace App
The Linode Marketplace lets you easily deploy software on a Compute Instance using Cloud Manager. See Get Started with Marketplace Apps for complete steps.
Log in to Cloud Manager and select the Marketplace link from the left navigation menu. This displays the Linode Create page with the Marketplace tab pre-selected.
Under the Select App section, select the app you would like to deploy.
Complete the form by following the steps and advice within the Creating a Compute Instance guide. Depending on the Marketplace App you selected, there may be additional configuration options available. See the Configuration Options section below for compatible distributions, recommended plans, and any additional configuration options available for this Marketplace App.
Click the Create Linode button. Once the Compute Instance has been provisioned and has fully powered on, wait for the software installation to complete. If the instance is powered off or restarted before this time, the software installation will likely fail.
To verify that the app has been fully installed, see Get Started with Marketplace Apps > Verify Installation . Once installed, follow the instructions within the Getting Started After Deployment section to access the application and start using it.
Configuration Options
- Supported distributions: Ubuntu 22.04 LTS
- Suggested minimum plan: All plan types and sizes can be used depending on your storage needs.
GlusterFS Options
- Linode API Token : The provisioner node will use an authenticated API token to create the additional components to the cluster. This is required to fully create the GlusterFS cluster.
Limited Sudo User
You need to fill out the following fields to automatically create a limited sudo user, with a strong generated password for your new Compute Instance. This account will be assigned to the sudo group, which provides elevated permissions when running commands with the sudo prefix.
Limited sudo user: Enter your preferred username for the limited user. No Capital Letters, Spaces, or Special Characters.
Locating The Generated Sudo Password A password is generated for the limited user and stored in a
.credentialsfile in their home directory, along with application specific passwords. This can be viewed by running:cat /home/$USERNAME/.credentialsFor best results, add an account SSH key for the Cloud Manager user that is deploying the instance, and select that user as an
authorized_userin the API or by selecting that option in Cloud Manager. Their SSH pubkey will be assigned to both root and the limited user.Disable root access over SSH: To block the root user from logging in over SSH, select Yes. You can still switch to the root user once logged in, and you can also log in as root through Lish .
Accessing The Instance Without SSH If you disable root access for your deployment and do not provide a valid Account SSH Key assigned to theauthorized_user, you will need to login as the root user via the Lish console and runcat /home/$USERNAME/.credentialsto view the generated password for the limited user.
") within any of the App-specific configuration fields, including user and database password fields. This special character may cause issues during deployment.- List of IP addresses to whitelist: A list of IP address that will be allowed to access GlusterFS cluster. These should be client IPs that will mount GlusterFS. SSL certificates will be created for the provided IP addresses.
Getting Started After Deployment
GlusterFS is now installed and ready to use!
Before you can use your new GlusterFS cluster, your clients will need to install a single dependency to mount GlusterFS as a filesystem:
- On every client node, install the GlusterFS client:
sudo apt install glusterfs-clientNext, ensure that the GlusterFS client knows we are using SSL certificates. We’ll create the
secure-accessfile. Do this on every client node:mkdir /var/lib/glusterd touch /var/lib/glusterd/secure-accessGrab the certificate for each respective client from the first GlusterFS instance.
If during the creation of the cluster you provided client IPs, you will find SSL certificates on the first GlusterFS server in
/usr/lib/ssl:(env) root@gluster1:/usr/lib/ssl# ls -l total 68 lrwxrwxrwx 1 root root 14 Mar 16 2022 certs -> /etc/ssl/certs -rw-r--r-- 1 root root 1630 Mar 28 14:40 client1.csr -rw------- 1 root root 3243 Mar 28 14:40 client1.key -rw-r--r-- 1 root root 1761 Mar 28 14:40 client1.pem -rw-r--r-- 1 root root 1630 Mar 28 14:40 client2.csr -rw------- 1 root root 3243 Mar 28 14:40 client2.key -rw-r--r-- 1 root root 1761 Mar 28 14:40 client2.pem -rw-r--r-- 1 root root 1630 Mar 28 14:40 client3.csr -rw------- 1 root root 3243 Mar 28 14:40 client3.key -rw-r--r-- 1 root root 1761 Mar 28 14:40 client3.pem -rw-r--r-- 1 root root 769 Mar 28 14:40 dhparams.pem -rw-r--r-- 1 root root 10584 Mar 28 14:40 glusterfs.ca -rw-r--r-- 1 root root 1635 Mar 28 14:40 glusterfs.csr -rw------- 1 root root 3243 Mar 28 14:40 glusterfs.key -rw-r--r-- 1 root root 1765 Mar 28 14:40 glusterfs.pem drwxr-xr-x 2 root root 4096 Mar 28 14:16 misc lrwxrwxrwx 1 root root 20 Feb 16 08:51 openssl.cnf -> /etc/ssl/openssl.cnf lrwxrwxrwx 1 root root 16 Mar 16 2022 private -> /etc/ssl/privateThis output assumes you created 3 client certificates! We’ll focus on installing the certificate for first client which is identified as
client1in the above output:- Copy the contents of
client1.pemfrom gluster1 and place it under/usr/lib/ssl/glusterfs.pemon client1 - Copy the contents of
client1.keyfrom gluster1 and place it under/usr/lib/ssl/glusterfs.keyon client1 - Copy the contents of
glusterfs.cafrom gluster1 and place it under/usr/lib/ssl/glusterfs.caon client1
- Copy the contents of
Finally, mount GlusterFS from the client nodes. Replace
gluster1with the private IP address of the first GlusterFS instance.mount -t glusterfs gluster1:/data-volume /mntUpdate the client’s
/etc/hostsfile. For example:192.168.139.160 gluster1 192.168.201.13 gluster2 192.168.230.83 gluster3Update the IP addresses to match your GlusterFS IP addresses.
Mount the GlusterFS filesystem automatically on boot.
- Edit the
/etc/fstabon the client nodes and append the following:
gluster1:/data-volume /MYMOUNT glusterfs defaults,_netdev,backup-volfile-servers=gluster2:gluster3 0 0Note: Update
MYMOUNTwith the location of where GlusterFS should be mounted. This could/mntas an example.- Edit the
Follow steps 1 through 6 for the remainder clients that need to be configured.
You are done!
Software Included
The GlusterFS Marketplace App installs the following software on your Linode:
| Software | Description |
|---|---|
| GlusterFS | Distributed network filesystem. |
| Firewalld | Firewalls to restrict port-level access to the cluster |
More Information
You may wish to consult the following resources for additional information on this topic. While these are provided in the hope that they will be useful, please note that we cannot vouch for the accuracy or timeliness of externally hosted materials.
This page was originally published on